As you can see there is login page with the prompt of login and password for logging into software, also there is you can see Register buttons and Change HID for changing the machine from directly used past integrations of HWID’s.
Author of Malware EvFLDev, from Syria, has provided account for software for 1000$ per month.
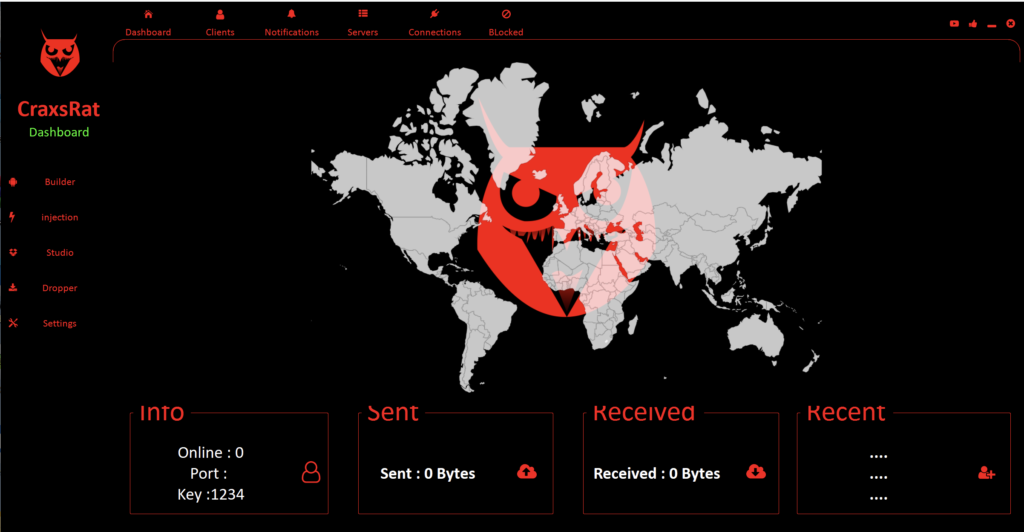
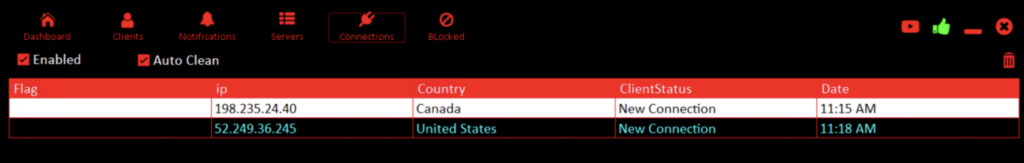
After of successfully logging into system we can see the main interface of control panel of CraxsRAT. You can see how many devices online, ports in use, also the key which one is using for connection between of client and server. After that you can see Live activity of packets in networks and recent activities like notifications, calls and SMS.

At the top of the program’s page you can see stuff like : Dashboard, Clients, Notifications, Servers, Connections, Blocked clients. Lets see what are they and what is their function.
At the menu of dashboard you can see main information about connection and keys of encryption codes.

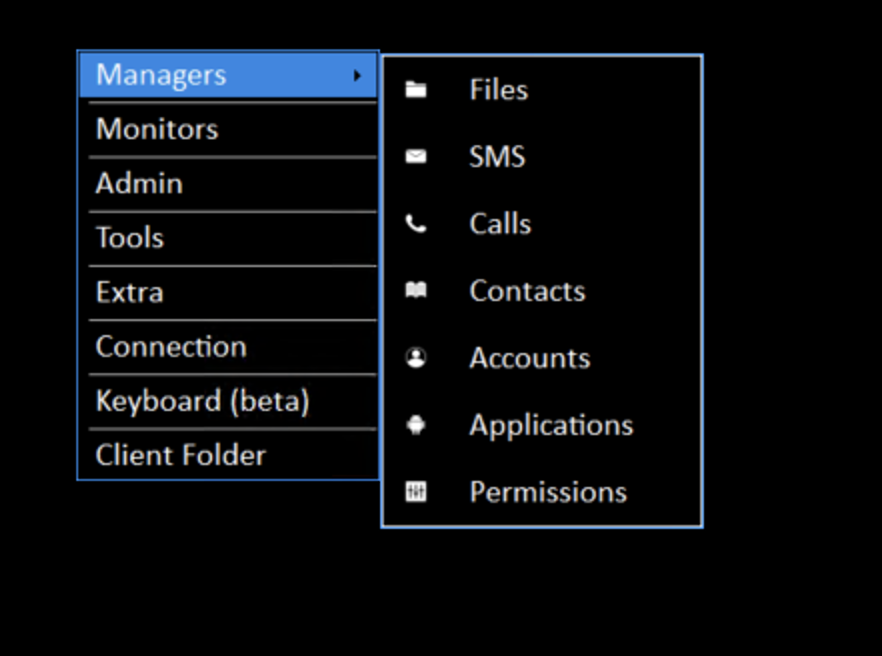
Here and there you can manage and see devices connected to backend and control them.
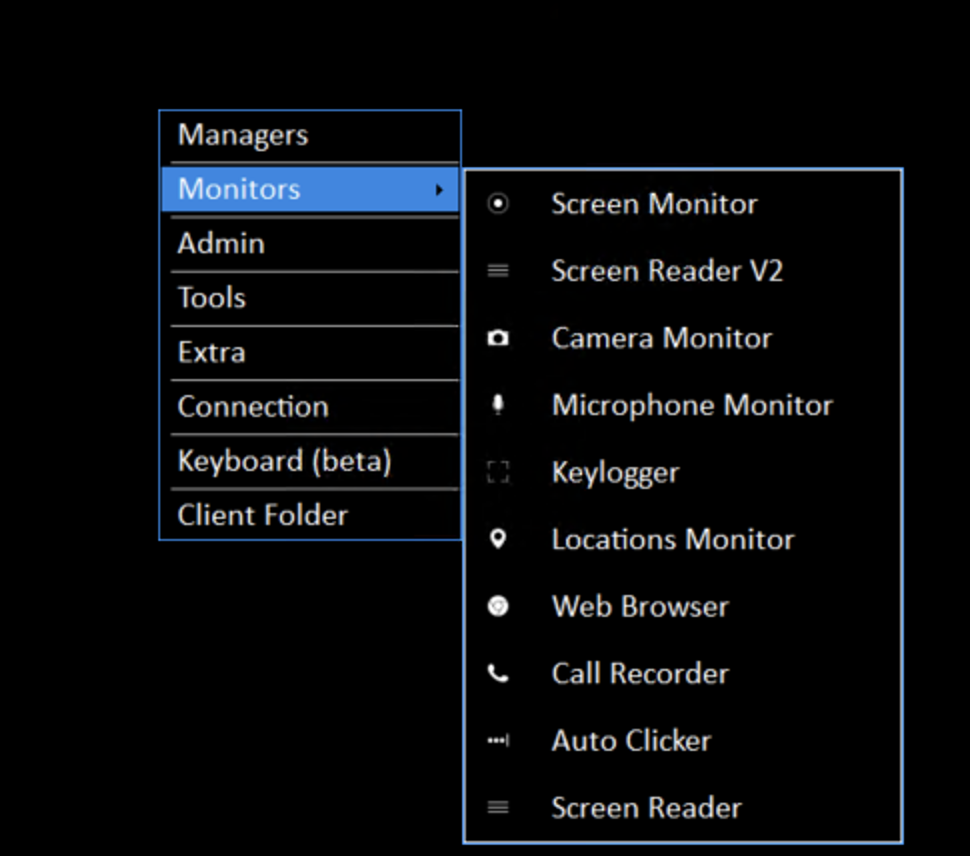
Screen Monitor is using for control the device’s screen. Screen Reader V2 is a version where you can also control the device’s screen without user interaction but without overlay and design. Just skeleton.

There you can manage the ports are activated on the interface and interact with them by changing the encryption keys, change active port, turn it on or off.
BUILDER OF CRAXSRAT
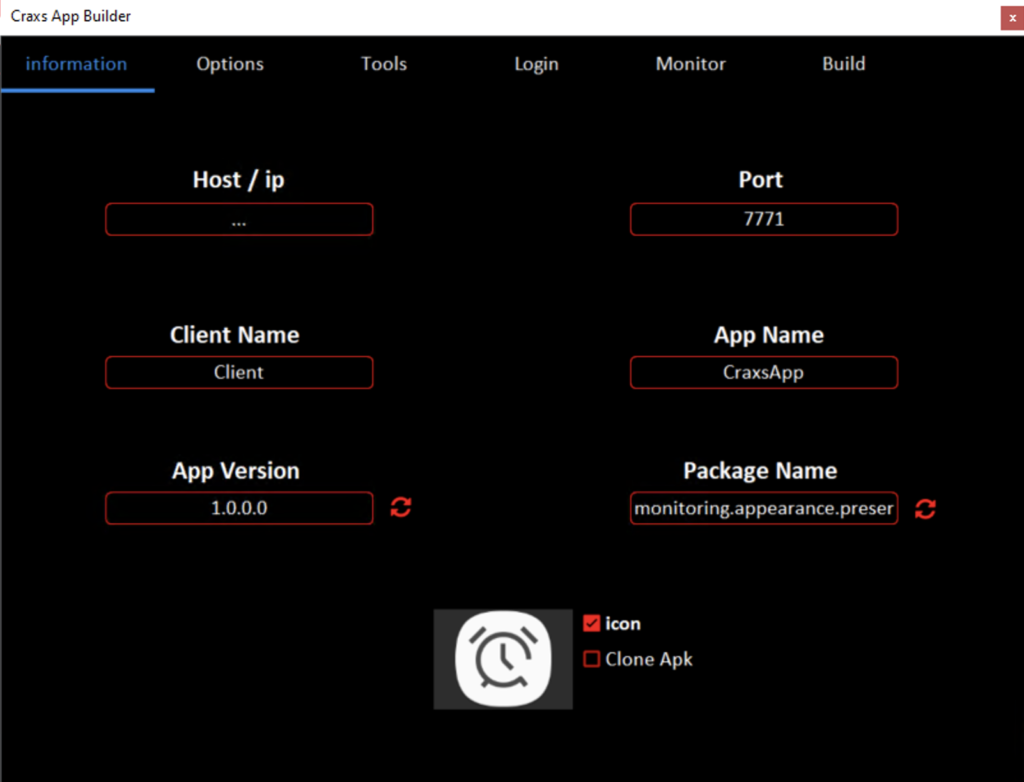
On the builder you can modify it for further use. For example, change IP address of server for connection of payload APK, Port for connection, Client name for difference the clients on the panel, App Name which one should appear while installing app file, package name, app version and icon.

Pack of readymade application you can use while building applications, as Youtube Lite, Hidden application, Google Translate and etc.
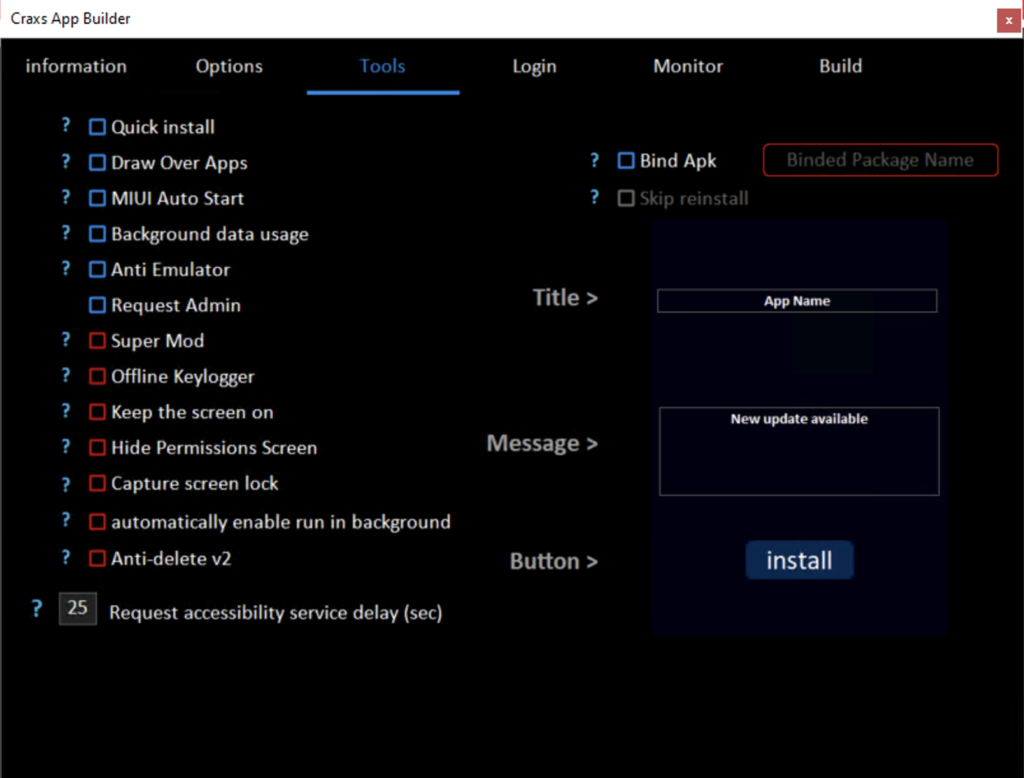
Opportunity to bind apk with another one, APK crypt and encryption.
Grab screen password and PIN code. Ask for accessibility services, quick installation.
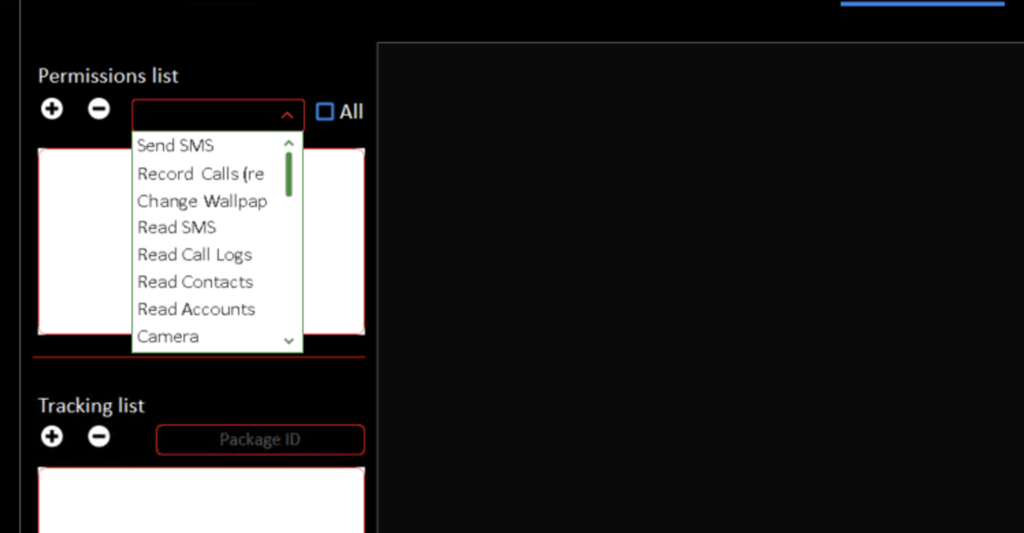
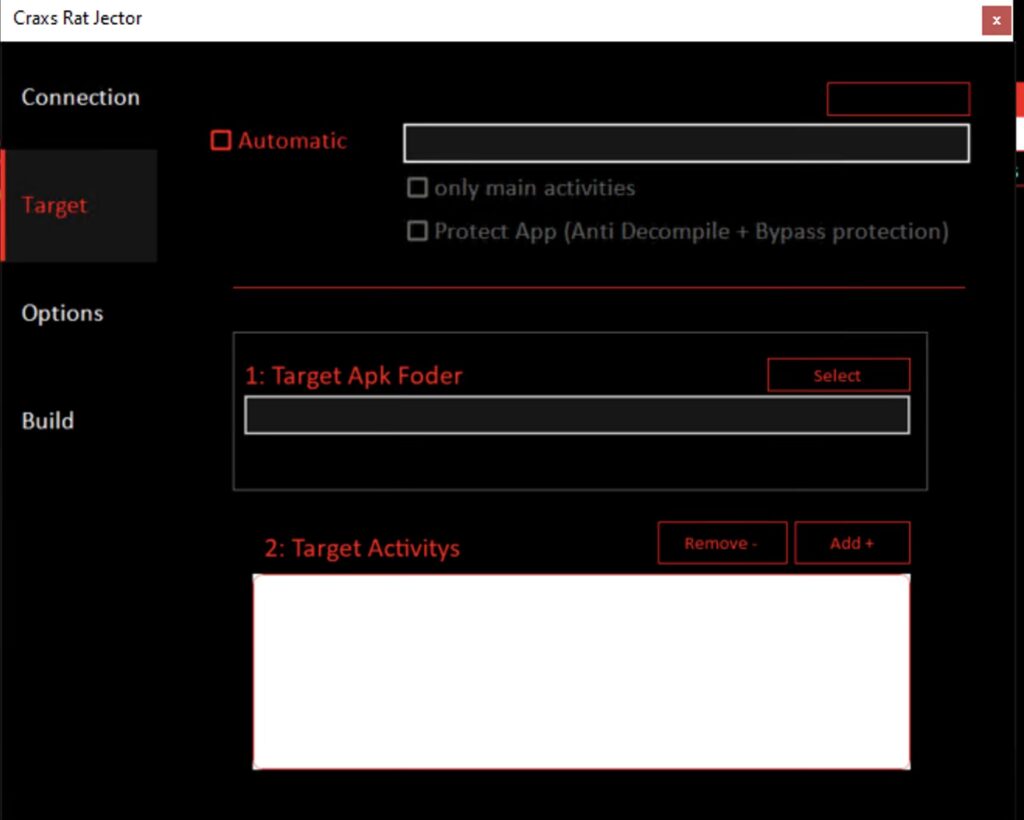
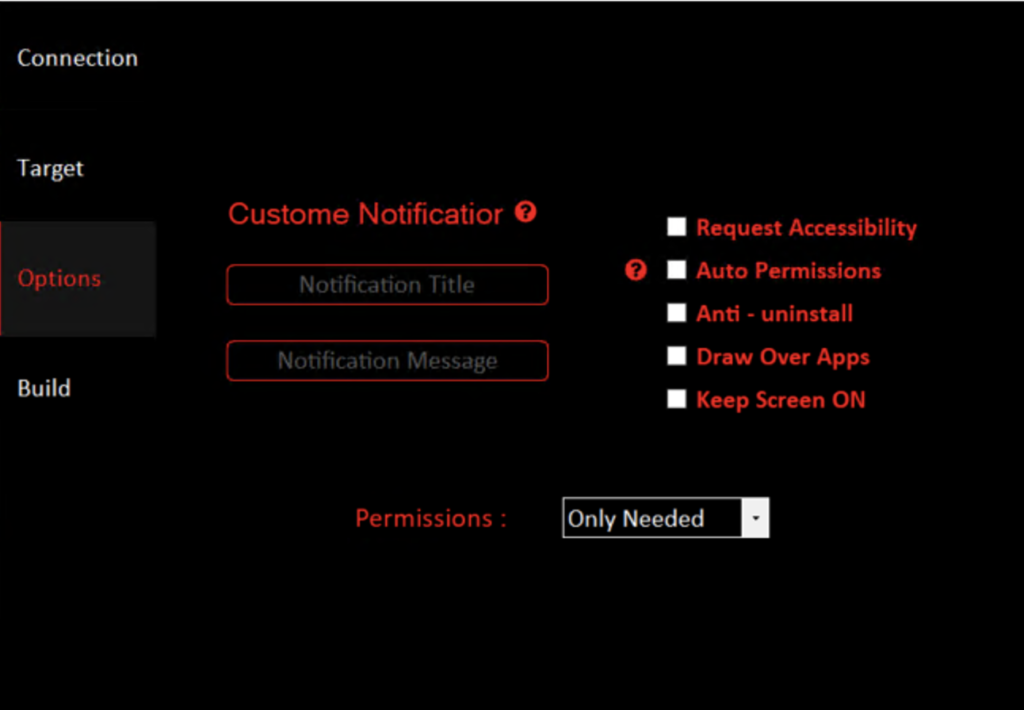
Apk injection can be used for injecting malicious code activity to the legitimate application what will cause the running payload while even running white and normally functioning applications.
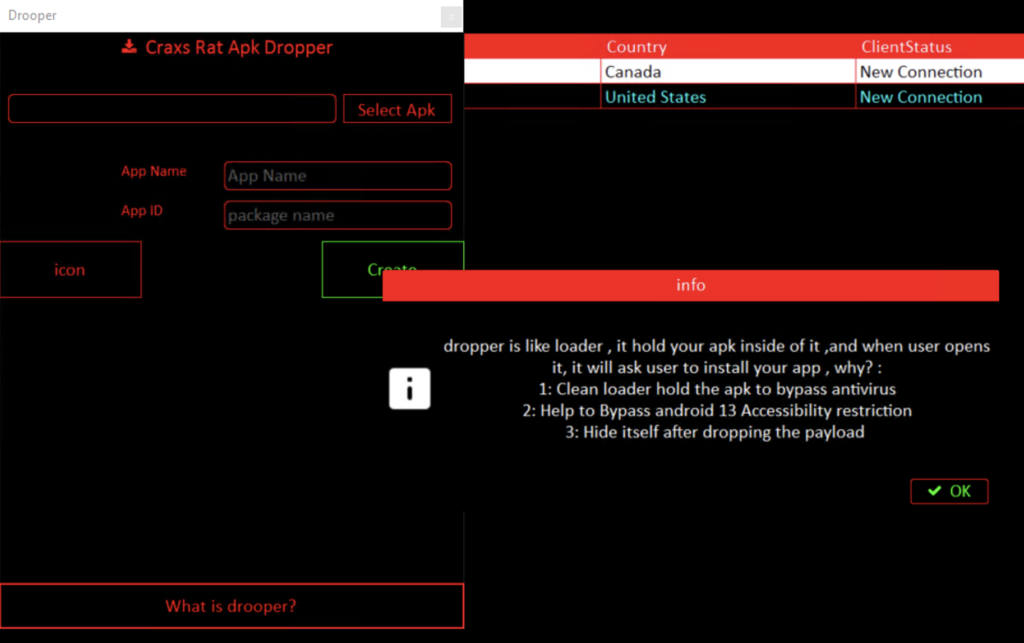
Dropper helps the threat actor to bypass restrictions for accessing to accessibility services on newest android versions ( Android 13 – Android 15 )