Here’s an expanded WordPress post about G700 RAT and CraxsRAT and their relationship as tools for remote administration and control:
Title: G700 RAT and CraxsRAT: Powerful Tools for Remote Administration and Their Ethical Dilemmas
Introduction
Remote Administration Tools (RATs) like G700 RAT and CraxsRAT have become household names in the realm of digital control. While they are designed to provide seamless remote access for legitimate purposes, their capabilities have also made them tools of interest for malicious actors. This post provides an in-depth overview of G700 RAT, CraxsRAT, their features, applications, and implications for cybersecurity.

What is G700 RAT?
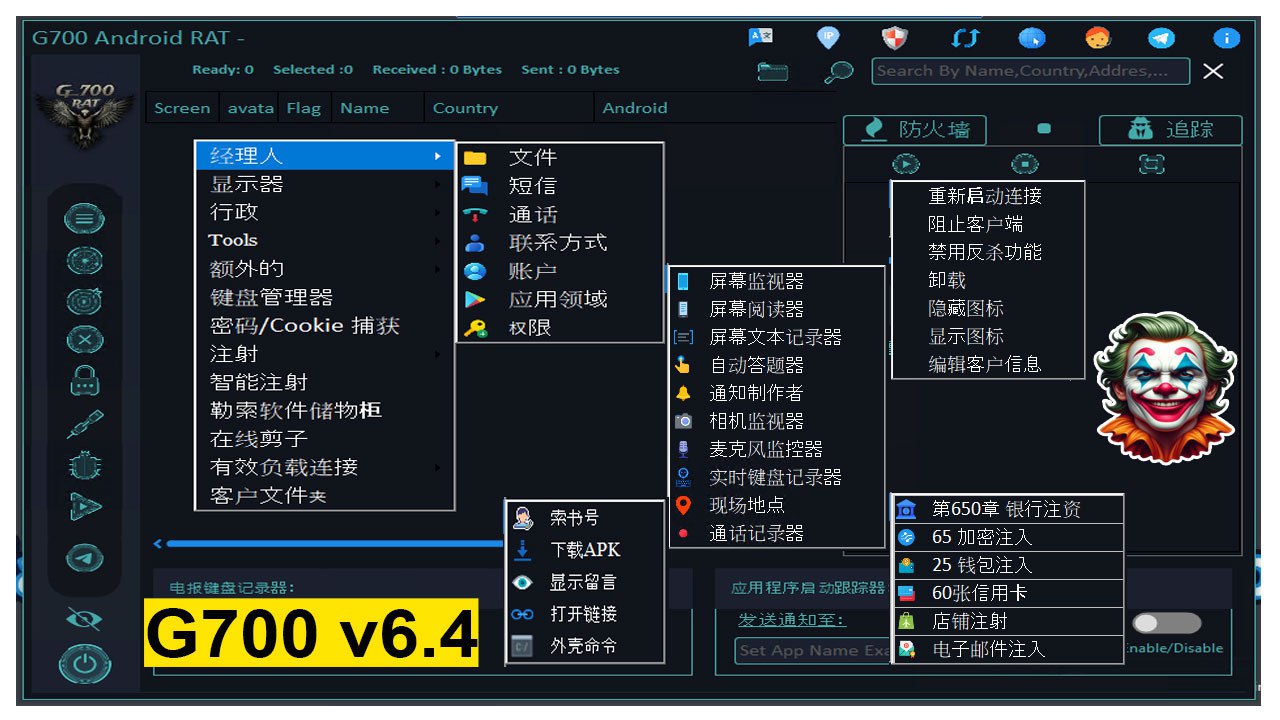
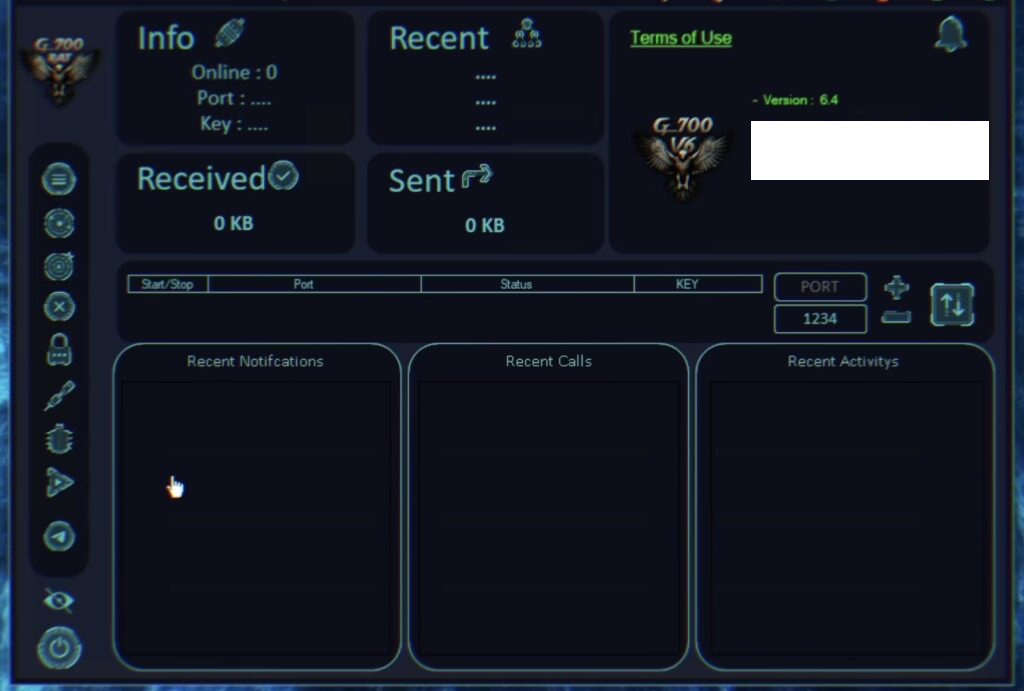
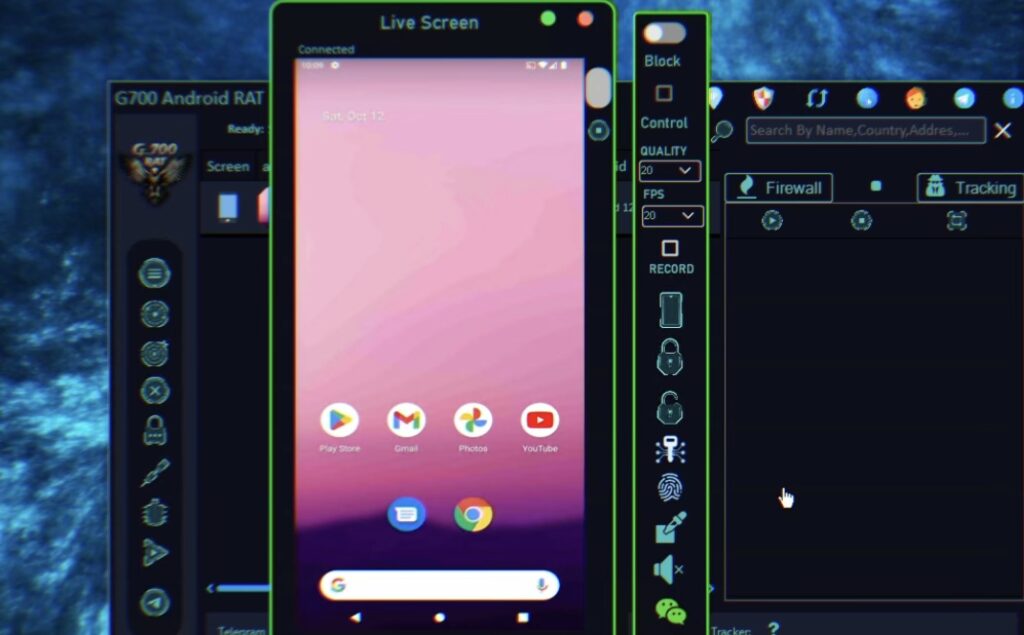
G700 RAT is a feature-rich remote administration tool that allows users to monitor and control devices remotely. Known for its speed and versatility, G700 RAT caters to both ethical users like IT professionals and unethical users with malicious intent. Its powerful capabilities make it one of the most sought-after tools in the RAT landscape.
Key Features of G700 RAT
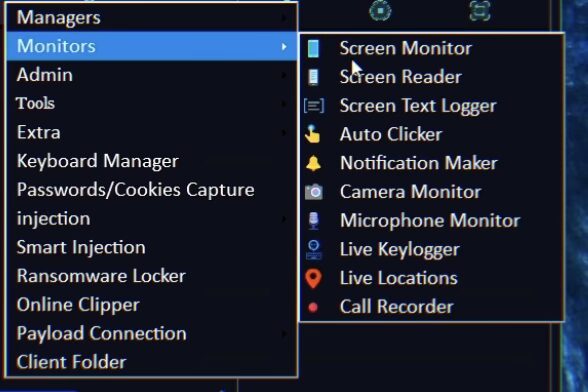
1. Multi-Platform Support
Like its sibling CraxsRAT, G700 RAT supports Windows, macOS, and Android devices, making it a versatile choice for administrators managing devices across platforms.
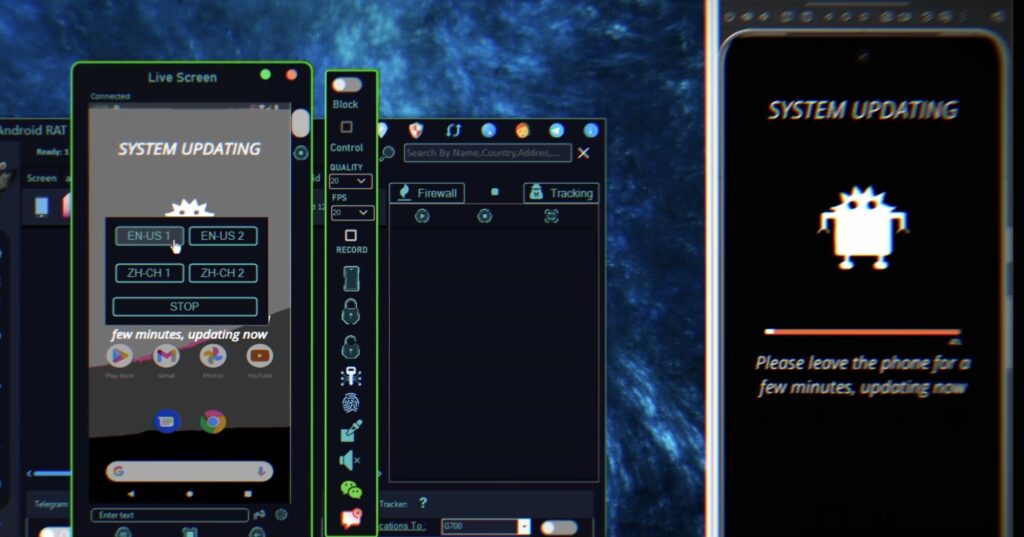
2. Stealth Operations
G700 RAT is designed to operate in stealth mode, ensuring its presence remains undetected on the target device. This feature is particularly controversial due to its potential misuse.
3. Advanced Keylogging
The tool includes a robust keylogger that records keystrokes, enabling users to capture sensitive data like passwords or private conversations.
4. File Management
With G700 RAT, users can browse, upload, and download files from the target device with ease.
5. Screen and Webcam Monitoring
The ability to view the target device’s screen and activate the webcam remotely allows for comprehensive surveillance.
6. Remote Shell Access
G700 RAT enables users to execute commands directly on the target system via a remote shell interface.
7. Network Scanning
The RAT includes tools to scan networks and discover vulnerabilities or devices for further exploitation.
What is CraxsRAT?
CraxsRAT is another powerful RAT that shares many similarities with G700 RAT but introduces some additional enhancements in customization and persistent access. Both tools originate from the same lineage of advanced RAT development but target slightly different user needs.
CraxsRAT vs. G700 RAT
Feature G700 RAT CraxsRAT
Multi-Platform Support ✅ ✅
Keylogging ✅ ✅
Webcam Monitoring ✅ ✅
Persistent Backdoors ❌ ✅
Payload Customization ❌ ✅
User-Friendly UI ✅ ✅
While G700 RAT focuses on operational speed and stealth, CraxsRAT emphasizes long-term access and payload flexibility.
How Do These RATs Work?
Both G700 RAT and CraxsRAT operate on a client-server model:
1. Client Side: The administrator’s device hosts the client interface, serving as the command center.
2. Server Side (Stub): A payload (or stub) is created and deployed to the target device. Once executed, the payload establishes a connection back to the client.
3. Remote Control: The attacker or administrator can monitor, control, or extract data from the target device through this connection.
The payload delivery methods often include:
• Phishing emails with malicious attachments
• USB drives with preloaded stubs
• Exploits targeting software vulnerabilities
Ethical Applications of G700 RAT and CraxsRAT
Despite their controversial nature, both tools have legitimate uses:
1. IT Administration
System administrators use these tools for remote troubleshooting, updates, and monitoring across enterprise networks.
2. Parental Control
Parents may use G700 RAT or CraxsRAT to monitor their children’s online activities, ensuring safe and responsible device usage.
3. Lost Device Recovery
The ability to track and control devices remotely can help recover stolen or misplaced devices.
4. Employee Monitoring
Organizations may employ these tools to ensure compliance with workplace policies, especially for remote teams.
Malicious Use Cases
Unfortunately, tools like G700 RAT and CraxsRAT are frequently exploited for:
1. Unauthorized Surveillance
Hackers can activate cameras and microphones without the victim’s consent, violating privacy laws.
2. Data Theft
Attackers use keylogging and file access features to steal credentials, financial data, or intellectual property.
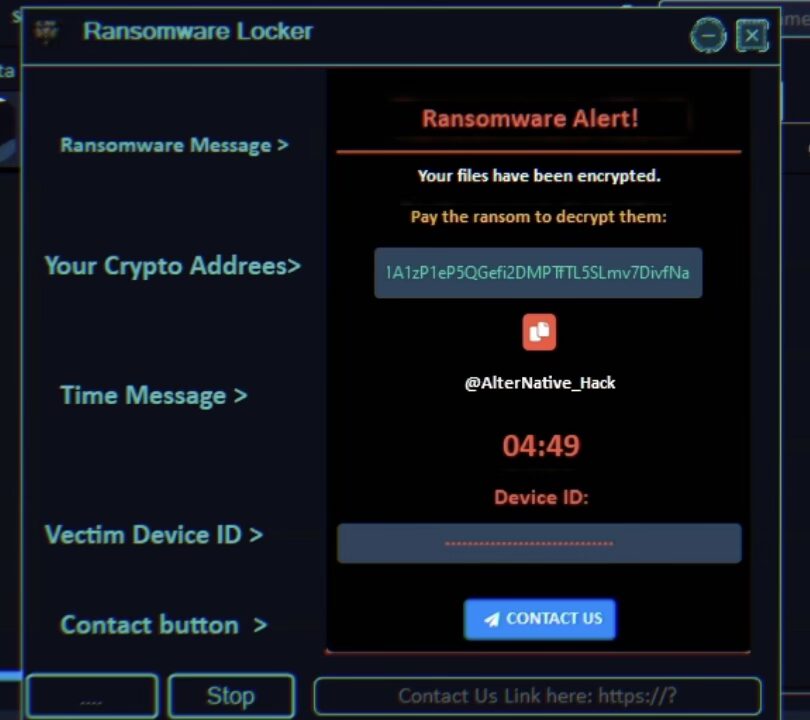
3. Spyware Distribution
Compromised devices are often used to distribute additional malware, including ransomware and spyware.
4. Botnet Creation
RATs can turn infected devices into part of a botnet, facilitating large-scale cyberattacks.
How to Protect Yourself from G700 RAT and CraxsRAT
To avoid falling victim to these powerful tools, follow these cybersecurity best practices:
1. Antivirus and Anti-Malware Software
Install reputable antivirus software, such as Avast, to detect and block malicious RAT payloads.
2. Regular Software Updates
Keep your operating system and applications up-to-date to patch vulnerabilities.
3. Avoid Suspicious Links
Do not open email attachments or click on links from unknown sources.
4. Use Firewalls
Enable firewalls to block unauthorized connections to your device.
5. Monitor Permissions
Regularly review app permissions to ensure no unauthorized applications have access to your device’s camera, microphone, or files.
Legal and Ethical Implications
Using G700 RAT or CraxsRAT without explicit consent is illegal in most jurisdictions. Violations include:
• Privacy Invasion: Unauthorized access to personal devices.
• Data Breach: Theft of sensitive information.
• Cybercrime Facilitation: Using RATs for hacking or distributing malware.
Ethical users must obtain clear permission before deploying these tools. Misuse can lead to severe legal consequences, including fines and imprisonment.
Future of Remote Administration Tools
As technology advances, tools like G700 RAT and CraxsRAT will continue to evolve. Key trends include:
1. AI Integration
Artificial intelligence will enhance RAT functionality, automating processes like vulnerability detection and exploitation.
2. Stronger Regulations
Governments worldwide are likely to enforce stricter laws on RAT usage and distribution.
3. Improved Cybersecurity
As RATs become more sophisticated, so will cybersecurity measures, creating a constant push-and-pull dynamic.
Conclusion
G700 RAT and CraxsRAT represent the dual-edged nature of remote administration tools. On one hand, they offer incredible utility for IT professionals, parents, and organizations. On the other, they pose significant risks when misused for malicious purposes.
Understanding these tools’ capabilities, ethical considerations, and potential consequences is crucial for navigating the complex landscape of remote administration and cybersecurity.