Here’s a detailed 2000-word WordPress post about Craxsrat 7.6:
Title: Craxsrat 7.6: The Ultimate Remote Administration Tool – Features, Benefits, and Security Implications
Introduction
Remote administration tools (RATs) have gained significant attention in the modern tech landscape. Whether used for legitimate remote support or less ethical purposes, these tools showcase the vast capabilities of technology. Among the leading solutions, Craxsrat 7.6 stands out as a robust and feature-rich tool. This post dives deep into the workings, features, use cases, and potential risks associated with Craxsrat 7.6.
What is Craxsrat 7.6?
Craxsrat 7.6 is the latest version of a remote administration tool designed for controlling and monitoring devices remotely. Initially created for legitimate administrative purposes, Craxsrat has found dual uses:
1. Ethical Applications: IT administrators use it for troubleshooting, monitoring systems, and offering support to clients.
2. Unethical Use Cases: Some individuals exploit its powerful features for spying, stealing sensitive data, or gaining unauthorized access.
This duality makes Craxsrat 7.6 both an incredibly useful tool and a potential cybersecurity threat.
Features of Craxsrat 7.6
Craxsrat 7.6 introduces several advanced features, making it one of the most powerful RATs available:
1. Real-Time Device Monitoring
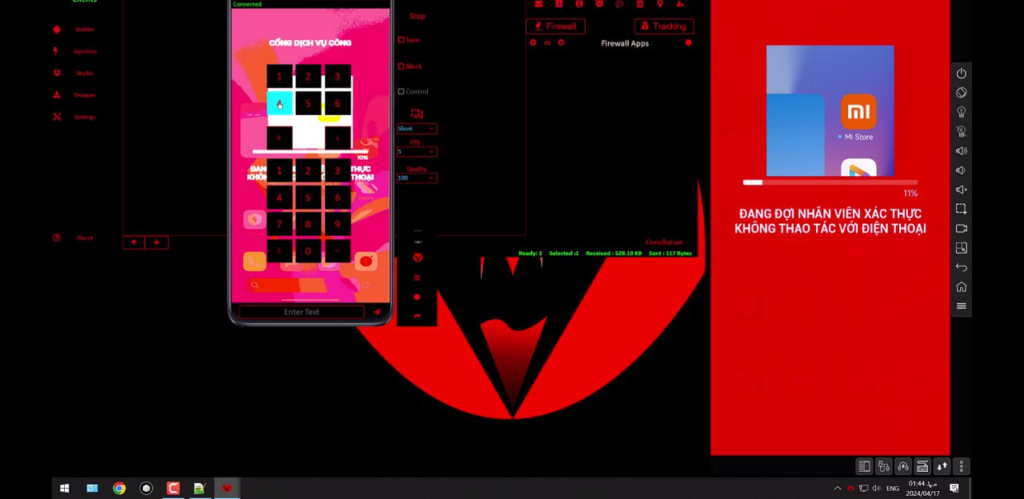
Craxsrat enables administrators to monitor the target device in real time. This includes access to system information, running processes, and performance metrics, making it an ideal tool for IT professionals.
2. Remote File Access and Management
With Craxsrat, you can browse, upload, download, or delete files on the target system. The interface simplifies navigating file systems, making remote file management seamless.
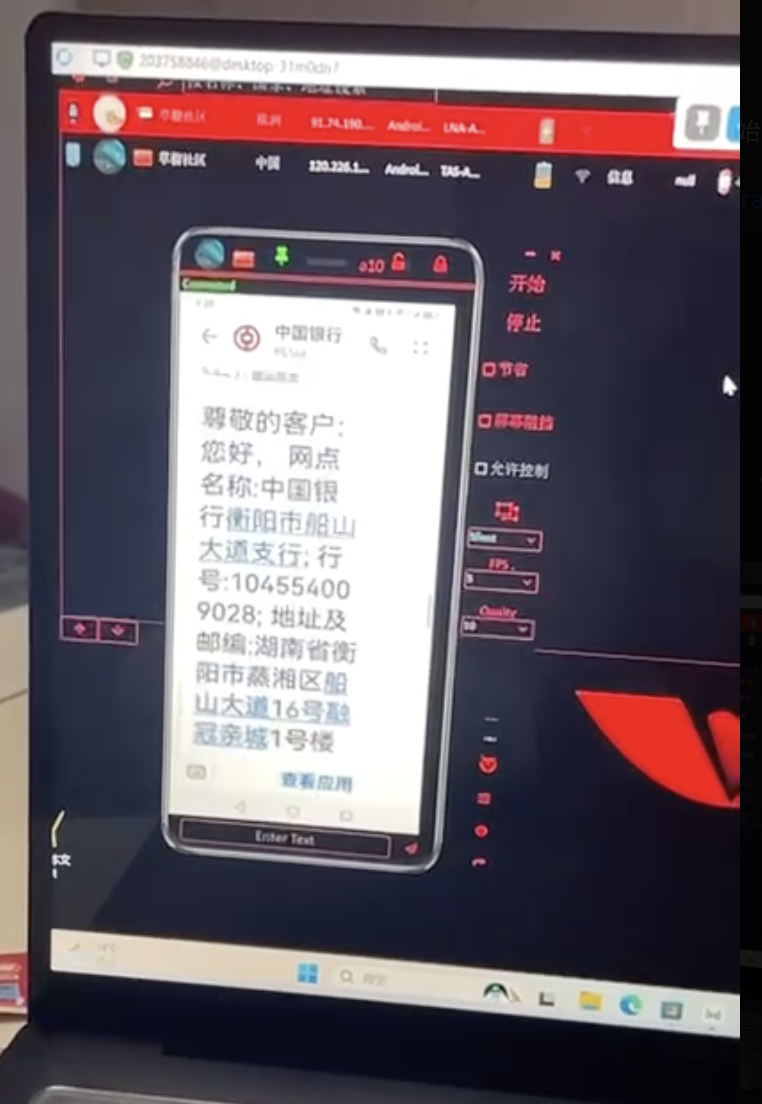
3. Keylogging
One of the most controversial features, Craxsrat’s built-in keylogger records keystrokes from the target device. This feature is often used for unethical purposes, such as stealing passwords or sensitive information.
4. Camera and Microphone Control
Craxsrat allows users to activate the target device’s camera and microphone, enabling remote surveillance. This feature is frequently cited in discussions about privacy risks and ethical concerns.
5. Advanced Multi-Platform Support
Craxsrat 7.6 supports multiple operating systems, including Windows, Android, macOS, and Linux. Its adaptability makes it a versatile tool for managing devices across different environments.
6. User-Friendly Interface
Despite its complex functionality, Craxsrat features an intuitive interface that makes it accessible to beginners and professionals alike.
7. Customizable Payloads
Craxsrat 7.6 allows users to create custom payloads for specific tasks, enabling highly tailored remote operations.
8. Persistent Backdoor Creation
Craxsrat can create persistent backdoors, ensuring long-term access to a target device even after reboots.
9. Network and Device Discovery
Users can scan for devices within a network and identify vulnerabilities for remote access.
How Craxsrat 7.6 Works
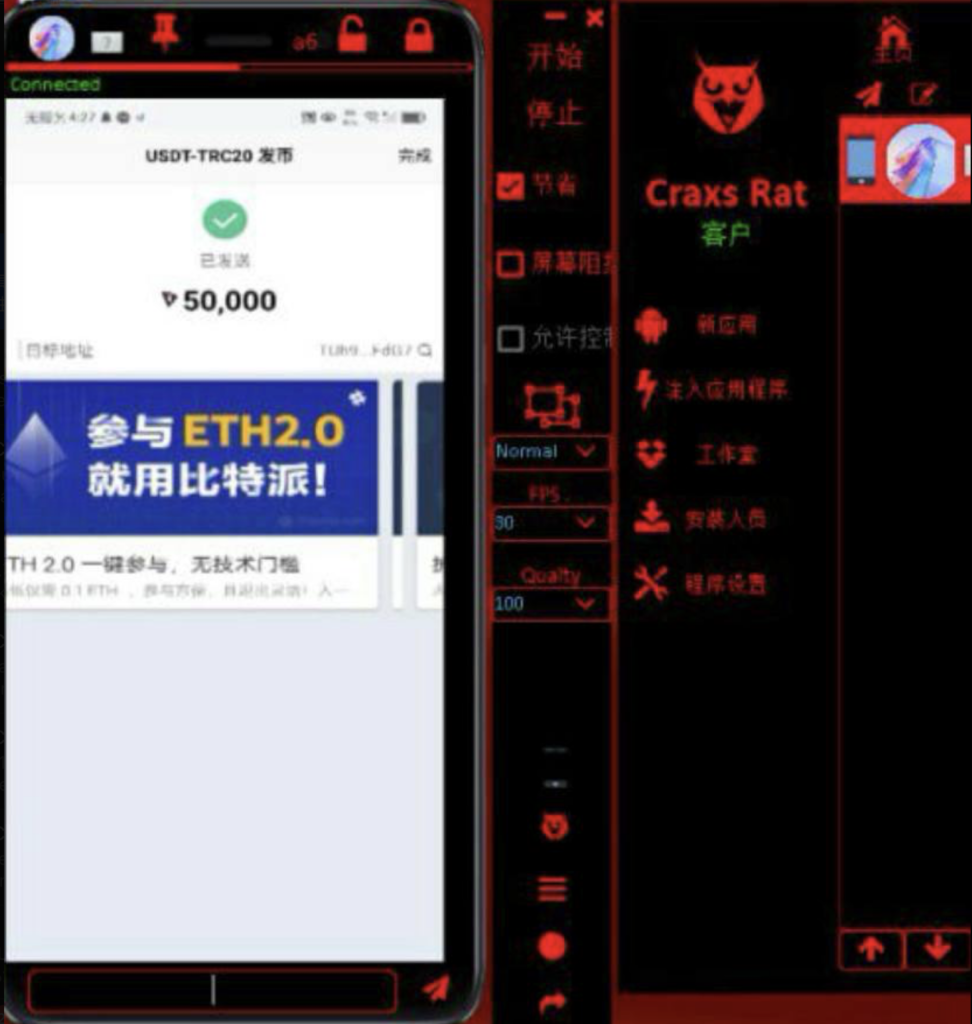
Craxsrat operates on a client-server model:
• Client: Installed on the administrator’s device. This serves as the command center for issuing instructions and viewing outputs.
• Server (or Stub): Installed on the target device. The server relays data back to the client while executing commands sent by the user.
Steps involved:
1. The user creates a payload (server stub) using Craxsrat.
2. The payload is delivered to the target device via email, USB drives, or social engineering tactics.
3. Once executed, the server stub connects to the client over the internet, allowing remote access.
Ethical Uses of Craxsrat 7.6
While controversial, Craxsrat 7.6 has legitimate applications, such as:
1. IT Support
IT administrators use Craxsrat to provide remote assistance, resolve system issues, and manage enterprise devices effectively.
2. Device Recovery
Craxsrat can be used to locate and recover stolen or lost devices by accessing their GPS location or IP address.
3. Parental Monitoring
Parents may use Craxsrat to monitor their children’s online activities, ensuring they are protected from inappropriate content or cyberbullying.
4. Employee Monitoring
Organizations can use Craxsrat to monitor employee activity, ensuring productivity and adherence to company policies.
Unethical and Malicious Uses
Despite its legitimate applications, Craxsrat is often exploited for unethical purposes. These include:
1. Hacking and Data Theft
Attackers use Craxsrat to steal sensitive information such as passwords, bank details, and personal data.
2. Surveillance and Spying
Unauthorized activation of cameras and microphones allows for invasive surveillance of victims.
3. Network Exploitation
Craxsrat enables attackers to scan and exploit vulnerabilities in networks, potentially leading to larger-scale cyberattacks.
4. Spreading Malware
Attackers may use Craxsrat to distribute other malicious payloads, such as ransomware or spyware.
Security Implications and Risks
1. Privacy Concerns
The ability to access cameras, microphones, and personal files without consent raises significant privacy concerns.
2. Data Breaches
Craxsrat can expose sensitive organizational data, leading to financial and reputational damage.
3. Malware Distribution
Compromised devices can be used as part of a botnet to distribute malware to other systems.
4. Legal Consequences
The unauthorized use of Craxsrat violates privacy laws and cybersecurity regulations in many jurisdictions, leading to severe legal consequences.
How to Protect Yourself from Craxsrat
To safeguard against Craxsrat and similar RATs, follow these best practices:
1. Install Antivirus Software
Use reliable antivirus solutions like Avast to detect and block malicious payloads.
2. Keep Software Updated
Ensure your operating system and applications are updated to patch known vulnerabilities.
3. Avoid Suspicious Links and Attachments
Be cautious when opening email attachments or clicking on unknown links, as these are common delivery methods for RAT payloads.
4. Enable Firewalls
Firewalls can prevent unauthorized connections between your device and a potential attacker’s client.
5. Regularly Monitor System Behavior
Unusual activity, such as slow performance or unexplained network traffic, could indicate a RAT infection.
6. Disable Unnecessary Features
Disabling camera and microphone permissions when not in use can limit an attacker’s capabilities.
Craxsrat 7.6 vs. Other RATs
Craxsrat 7.6 stands out due to its advanced features and ease of use. Here’s a comparison with other popular RATs:
Feature Craxsrat 7.6 njRAT DarkComet
Multi-Platform Support ✅ ❌ ✅
Customizable Payloads ✅ ✅ ❌
User-Friendly UI ✅ ❌ ✅
Persistent Backdoors ✅ ✅ ✅
Craxsrat’s combination of powerful features and user-friendly design makes it a preferred choice for both ethical and malicious users.
Legal and Ethical Considerations
The use of Craxsrat is a double-edged sword. While it has legitimate applications, unauthorized use is illegal and unethical. Laws regarding the use of RATs vary by country, but common violations include:
• Privacy Invasion: Accessing devices without consent.
• Data Theft: Stealing sensitive or personal data.
• Cybercrime Facilitation: Using RATs to distribute malware or engage in phishing campaigns.
Ethical users must ensure they have explicit permission before accessing another device with Craxsrat.
The Future of Remote Administration Tools
The evolution of tools like Craxsrat 7.6 reflects broader trends in remote access and cybersecurity. As technology advances, RATs will continue to become more sophisticated. Simultaneously, cybersecurity measures will evolve to counteract malicious use. Key trends to watch include:
• AI-Driven Security: AI-powered systems will improve detection and prevention of RAT-related threats.
• Stronger Regulations: Governments are likely to introduce stricter laws and enforcement against unauthorized RAT use.
• Encryption Advancements: Enhanced encryption technologies will protect legitimate RAT communications from interception.
Verdict
Craxsrat 7.6 is a powerful remote administration tool with a broad spectrum of applications. While its legitimate uses benefit IT administrators, parents, and organizations, its misuse poses significant security and ethical challenges. Understanding its capabilities and risks is essential for anyone interacting with this tool, whether for ethical purposes or as a potential victim.